What is Zero Trust?
Zero Trust is a security framework designed to protect organizations from the evolving landscape of cybersecurity threats. Unlike traditional security models that operate on the assumption that everything within an organization’s network can be inherently trusted, Zero Trust starts with the principle that no entity whether inside or outside the network should be trusted by default. This approach enforces the idea of “never trust, always verify,” ensuring that stringent security measures are applied universally.

YouTube
Just in Time Permissions Explained #Delinea #PAM #CyberSecurity
FORTIFY YOUR DEFENSES WITH ZERO TRUST NETWORK
What is ZTΝΑ?
- Zero Trust Network Access is a cybersecurity approach built on the idea of " never trust, always verify".
How does it work?
- Imagine your network is divided into smaller sections, like rooms in a house. ZTNA controls who can enter each room based on their identity and what they're trying to do.
- ZTNA also uses strong encryption to protect your data, so only authorised people can open it. It also monitors everything, adapting to new threats in realtime.
How can ZTNA help you?
- 1. It significantly improves your security posture by reducing risks of unauthorised access and data breaches.
- 2. It also enhances user experience by allowing secure access to resources from anywhere, on any device.
- 3. It is scalable and flexible, so it can grow with your business.
Implementing ZTNA:
- 1. Assess your current infrastructure and identify your critical assets.
- 2. Develop comprehensive control policies based on identity, device posture, and other factors.
- Finally, choose the right ZTNA solutions for your organization and train your staff on the new security procedures.
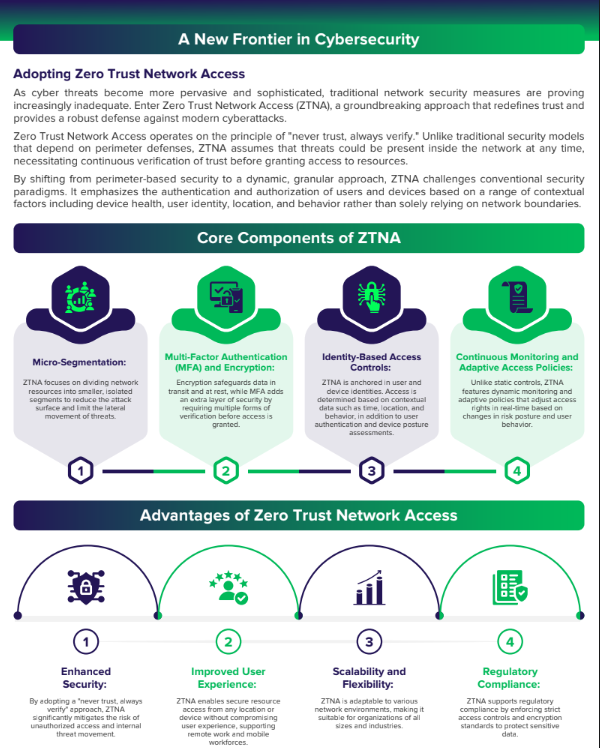
Adopting Zero Trust Network Access
As cyber threats become more pervasive and sophisticated, traditional network security measures are proving increasingly inadequate. Enter Zero Trust Network Access (ZTNA), a groundbreaking approach that redefines trust and provides a robust defense against modern cyberattacks. Zero Trust Network Access operates on the principle of “never trust, always verify.” Unlike traditional security models
that depend on perimeter defenses, ZTNA assumes that threats could be present inside the network at any time, necessitating continuous verification of trust before granting access to resources. By shifting from perimeter-based security to a dynamic, granular approach, ZTNA challenges conventional security paradigms. It emphasizes the authentication and authorization of users and devices based on a range of contextual factors including device health, user identity, location, and behavior rather than solely relying on network boundaries.
Micro-Segmentation: ZTNA focuses on dividing network resources into smaller, isolated segments to reduce the attack surface and limit the lateral movement of threats.
Multi-Factor Authentication (MFA) and Encryption: Encryption safeguards data in transit and at rest, while MFA adds an extra layer of security by requiring multiple forms of verification before access is granted.
Identity-Based Access Controls: ZTNA is anchored in user and device identities. Access is determined based on contextual data such as time, location, and behavior, in addition to user authentication and device posture assessments.
Continuous Monitoring and Adaptive Access Policies: Unlike static controls, ZTNA features dynamic monitoring and adaptive policies that adjust access rights in real-time based on changes in risk posture and user behavior.
Enhanced Security: By adopting a “never trust, always verify” approach, ZTNA significantly mitigates the risk of unauthorized access and internal threat movement.
Improved User Experience: ZTNA enables secure resource access from any location or device without compromising user experience, supporting remote work and mobile workforces.
Scalability and Flexibility: ZTNA is adaptable to various network environments, making it suitable for organizations of all sizes and industries.
Regulatory Compliance: ZTNA supports regulatory compliance by enforcing strict access controls and encryption standards to protect sensitive data.
Assessment and Planning: Review your current network architecture, identify critical assets, and evaluate readiness for ZTNA.
Policy Definition: Create detailed access control policies based on identity, device posture, and contextual factors.
Technology Selection: Choose ZTNA solutions that align with your organization’s security needs and infrastructure.
Pilot Deployment: Test ZTNA in a controlled environment to ensure its effectiveness before a full-scale rollout.
Continuous Monitoring and Optimization: Establish ongoing monitoring and optimization processes to adapt to evolving threats and maintain ZTNA effectiveness.
Conclusion
The evolving sophistication of cyber threats necessitates a departure from traditional network security methods. Zero Trust Network Access offers a revolutionary approach to cybersecurity, allowing organizations to adopt a proactive, dynamic stance on access management. By implementing ZTNA, organizations can enhance their security posture, reduce risks, and safeguard critical assets in an increasingly connected world.
As Zero Trust Network Access (ZTNA) becomes crucial for enhancing security, integrating it with existing IT systems is essential. While this might seem challenging, thoughtful design and implementation can seamlessly enhance security without disrupting operations.
Start with a thorough evaluation of your current IT infrastructure. This involves reviewing access controls, identifying critical assets, analyzing network architecture, and understanding user behavior patterns.
1.Identity and Access Management (IAM) Systems: Integrate ZTNA with IAM systems to enhance access control based on user identity.
2. Network Security Appliances: Configure ZTNA solutions to work with existing firewalls, intrusion detection systems (IDS), and other network security appliances to enforce access controls and detect threats.
3. Endpoint Security Solutions: Integrate ZTNA with endpoint security solutions like mobile device management (MDM) platforms, antivirus software, and endpoint detection and response (EDR) technologies to ensure secure access from all endpoints.
4. Cloud Services: Expand ZTNA capabilities to cloud environments by integrating with native security controls of cloud service providers and cloud access security brokers (CASBs).
Choose ZTNA solutions that seamlessly integrate with your existing IT infrastructure. Look for solutions that support industry-standard protocols, offer flexible deployment options, and are compatible with your current IAM, networking, and security technologies.
Conduct a pilot integration in a controlled environment to assess ZTNA’s performance, compatibility, and effectiveness with your current systems. This helps identify potential issues and ensures a smooth full-scale implementation.
Effective ZTNA integration requires organizational buy-in and alignment. Provide comprehensive training to end users, security teams, and IT staff on ZTNA benefits, new access control policies, and security best practices. Emphasize the importance of adhering to security guidelines to ensure a smooth transition.
After integrating ZTNA, establish procedures for continuous monitoring and optimization. Regularly review access logs, user behavior analytics, and security alerts to identify anomalies and potential risks. Continuously refine access policies based on feedback and evolving security needs.
Conclusion
Integrating Zero Trust Network Access with your existing IT infrastructure is a strategic move for organizations aiming
to enhance their cybersecurity posture. By carefully evaluating infrastructure, identifying integration points, selecting compatible solutions, piloting integration, providing training, and implementing robust monitoring, organizations can effectively incorporate ZTNA into their security strategy. This approach enhances security while maintaining productivity and usability, allowing you to navigate the evolving cybersecurity landscape with confidence and safeguard your organization’s vital assets.
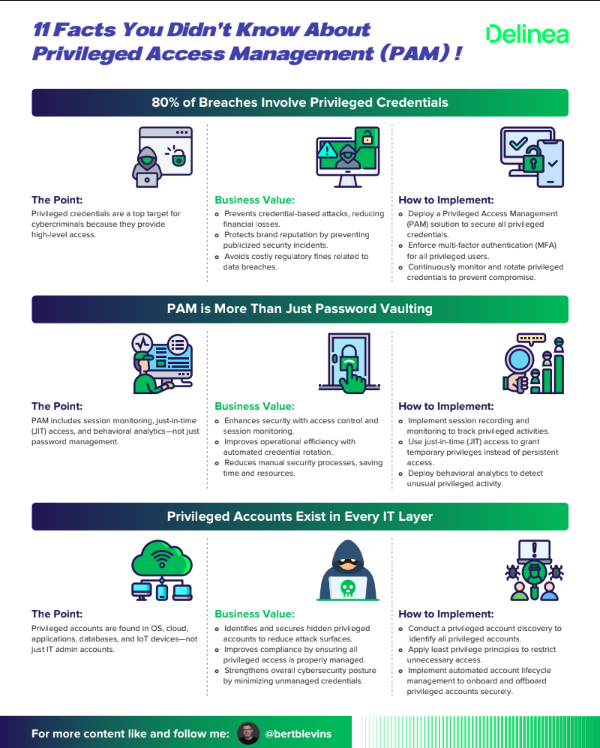
11 Facts You Didn't Know About Privileged Access Management (PAM) !
80% of Breaches Involve Privileged Credentials
The Point: Privileged credentials are a top target for
cybercriminals because they provide
high-level access.
Business Value: Prevents credential-based attacks, reducing
financial losses.
o Protects brand reputation by preventing publicized security incidents.
How to Implement: Deploy a Privileged Access Management
(PAM) solution to secure all privileged
credentials.
PAM is More Than Just Password Vaulting
The Point: PAM includes session monitoring, just-in-time
(JIT) access, and behavioral analytics—not just
password management.
Business Value:Enhances security with access control and session monitoring.
How to Implement: Implement session recording and
monitoring to track privileged activities.
Privileged Accounts Exist in Every IT Layer
The Point: Privileged accounts are found in OS, cloud,
applications, databases, and IoT devices—not
just IT admin accounts.
Business Value: Identifies and secures hidden privileged
accounts to reduce attack surfaces.
How to Implement: Conduct a privileged account discovery to
identify all privileged accounts.
Service Accounts Are a Major Security Risk
The Point: Service accounts often have static credentials and
excessive privileges, making them easy targets for
attackers.
Business Value: Prevents service account exploitation, reducing
risk of lateral movement attacks.
How to Implement: Replace hardcoded service account credentials
with a secure vault.
Zero Trust Relies on PAM
The Point: Zero Trust security requires strict access verification,
which PAM enforces through least privilege access
and MFA..
Business Value: Strengthens Zero Trust by enforcing strict access
control.
How to Implement: Enforce least privilege access and role-based
access control (RBAC).
Humans Aren’t the Only Users
The Point: Machine identities (APIs, bots, scripts) also have
privileged access and need to be secured like human
users.
Business Value: Reduces risk of machine identity abuse by
securing non-human accounts.
How to Implement: Use secrets management solutions to store and
rotate API keys and credentials securely.
Session Recording is a Double-Edged Sword
The Point: Session recording enhances security but must be
managed properly to avoid privacy risks.
Business Value: Provides strong security oversight while balancing
privacy concerns.
How to Implement: Ensure encrypted and secure storage of recorded
sessions.
Privileged Access Extends to Cloud and DevOps
The Point: Traditional PAM focused on on-premise
environments, but modern IT includes cloud, DevOps,
and CI/CD pipelines.
Business Value: Secures cloud and DevOps environments,
preventing unauthorized access.
How to Implement: Use cloud-native PAM solutions that integrate with
AWS, Azure, and GCP.
PAM Helps with Compliance (and Saves You from Fines)
The Point: Regulations like GDPR, HIPAA, PCI DSS, and NIST
require strict privileged access controls.
Business Value: Helps organizations avoid hefty fines by meeting
compliance requirements.
How to Implement: Conduct regular compliance audits of privileged access.
Privileged Credential Abuse is Hard to Detect Without PAM
The Point: Malicious privileged activity often appears normal,
making it difficult to detect without PAM monitoring.
Business Value: Prevents costly security incidents by identifying and stopping credential abuse.
How to Implement: Deploy real-time privileged activity monitoring.
What Are Zero Trust Remote Apps?
Zero Trust Remote Applications are applications accessed remotely under a Zero Trust security framework. Unlike traditional models that trust users within a network perimeter, Zero Trust requires continuous verification of every user’s identity, device health, and contextual factors before granting access to any application. This ensures that remote app access is granted only to authorized users on secure devices, minimizing risk and protecting sensitive data.
Why Zero Trust for Remote Apps Matters
Traditional remote access methods like VPNs often grant broad network access, which can expose organizations to unauthorized entry and lateral movement by attackers. With the increasing reliance on cloud and remote work environments, these risks are amplified. Zero Trust for remote apps addresses these challenges by enforcing strict, context-aware access controls that improve security without compromising user experience, enabling safe and seamless remote application use.
Secure your remote apps today with Zero Trust.
Explore our solutions, request a demo, or consult with our experts.

Core Principles of Zero Trust for Remote Apps
Continuous Authentication and Authorization: Every session is verified continuously to ensure ongoing compliance with security policies.
Least Privilege Access: Users and devices receive only the minimal access necessary based on their role and security posture.
Microsegmentation and Isolation: Applications and sessions are segmented and isolated to prevent lateral movement and contain potential breaches.
Features & Benefits
Granular Access Control: Dynamic policies adjust access rights based on real-time analysis of user identity, device status, geographic location, and risk factors.
Application Isolation: Each remote app session is sandboxed, preventing cross-application attacks and unauthorized data sharing.
Multi-Factor Authentication (MFA): Strong authentication methods protect access by requiring additional verification layers.
Session Monitoring & Analytics: Gain real-time insights into user behavior and detect suspicious activities swiftly.
Cloud & Hybrid Environment Support: Securely connect users to applications hosted both in the cloud and on-premises.
Improved User Experience: Enjoy fast, secure, and frictionless remote app access without the latency and complexity associated with traditional VPNs.

Use Cases
- Securing Remote Workforce Access: Enable employees to safely access SaaS and enterprise applications from anywhere.
- Protecting Sensitive Applications: Especially critical in regulated industries such as healthcare and finance.
- Third-Party and Vendor Access: Provide controlled, monitored access to partners and contractors with strict policies.
- VPN Replacement: Transition from legacy VPNs to modern, scalable Zero Trust solutions for enhanced security and performance.
Security & Compliance
- Zero Trust remote app access solutions help organizations comply with regulations including HIPAA, GDPR, PCI-DSS, and more. Through comprehensive audit trails, session recordings, and detailed compliance reporting, organizations can demonstrate strong governance and respond quickly to audits or security incidents.
Implementation Guidance
- Deployment Steps: Learn how to smoothly transition from traditional remote access solutions to Zero Trust remote app access within your existing IT infrastructure.
- Integration Capabilities: Connect seamlessly with Identity and Access Management (IAM) systems, Privileged Access Management (PAM) tools, and endpoint security platforms to create a unified security posture.
Zero Trust Overview
The Zero Trust model was born out of the need to address modern security challenges posed by mobile workforces, cloud-based resources, and increasingly sophisticated cyber-attacks. With the shift towards more distributed network environments, legacy perimeter-based security strategies have become inadequate. Zero Trust, therefore, redefines the way organizations approach cybersecurity by assuming that potential threats can exist both outside and inside the traditional network boundary.
Key components of a Zero Trust framework include:
- 01. Continuous Verification
- 02. Least Privilege Access
- 03. Micro-Segmentation
- 04. Multi-Factor Authentication (MFA)
- 05. Real-Time Monitoring and Analytics
- 06. Device Security
Benefits of Zero Trust
Enhanced Security Posture:
ero Trust significantly reduces the risk of data breaches by limiting access and ensuring continuous verification.
Reduced Attack Surface:
With micro-segmentation and least privilege access, the potential spread of an attack is minimized.
Increased Visibility:
Organizations gain more visibility into who is accessing their resources and how they are interacting with them, allowing for better security management.
Improved Compliance:
The robust policies and logging mechanisms inherent in Zero Trust can help organizations meet regulatory requirements more effectively.
Conclusion
The Zero Trust security framework marks a fundamental shift in how organizations approach cybersecurity. By assuming that no entity can be trusted by default, Zero Trust enforces robust security practices that mitigate the risk of breaches and strengthen defenses against both external and internal threats. Adopting Zero Trust may involve considerable initial effort and resources, but its long-term benefits in terms of security and compliance make it an essential strategy for the modern digital enterprise.

Zero Trust Principles
The Zero Trust security model is built on a set of guiding principles that fundamentally redefine how access to resources is managed and controlled. These principles prioritize strict authentication, continuous validation, and a granular approach to resource protection to secure organizations against modern cyber threats. Below, we delve into the core principles that drive the Zero Trust approach:
- Never Trust, Always Verify
- Least Privilege Access
- Micro-Segmentation
- Continuous Monitoring and Analytics
- Comprehensive Device Security
- Multi-Factor Authentication (MFA)
Why Zero Trust is Essential for Remote Applications
The shift to remote work has posed significant security challenges for organizations worldwide. As more employees access company resources from locations outside the traditional network perimeter, new vulnerabilities have emerged that legacy security models are ill-equipped to handle. Zero Trust is uniquely suited to address these challenges, providing robust security measures that help organizations safeguard their data and operations in remote work environments.
1. Mitigating Unauthorized Access
Remote work often involves users connecting to company systems from various locations and networks, which can increase the risk of unauthorized access. With a Zero Trust framework, every access request is thoroughly verified, ensuring that only authenticated users with the right permissions can access resources. By enforcing continuous verification, Zero Trust minimizes the chances of unauthorized access, even when employees work remotely.
2. Protecting against Compromised Devices
Remote work can lead to situations where employees use personal devices or work-issued devices that may lack the latest security updates. Such devices are more susceptible to being compromised by malware or other cyber threats. Zero Trust addresses this by enforcing stringent device security checks, ensuring that only compliant devices can access sensitive resources. Continuous device health verification prevents compromised or non-compliant devices from becoming points of entry for attackers.
3. Reducing the Risk of Data Breaches
One of the most significant risks of remote work is data breaches due to insecure connections or unauthorized data transfers. Zero Trust incorporates encryption protocols and strict data access controls that help prevent sensitive information from being exposed. Micro-segmentation also ensures that even if an attacker gains access to one part of the network, their lateral movement is limited, reducing the risk of large-scale data breaches.
4. Improving Response to Emerging Threats
Zero Trust’s emphasis on continuous monitoring and real-time analytics is particularly valuable in remote work settings where threats can emerge quickly and unpredictably. By employing AI-driven monitoring tools, organizations can detect and respond to suspicious activities faster, providing enhanced security even when the workforce is geographically dispersed. The use of automation in threat detection and response further strengthens an organization’s ability to contain potential breaches before significant damage occurs.
5. Supporting Compliance in Remote Environments
Many industries are subject to regulations that require organizations to protect data and ensure secure access to information. Zero Trust’s approach to access control, user authentication, and continuous monitoring helps organizations maintain compliance with data protection standards even in remote settings. By adhering to the principles of Zero Trust, organizations can demonstrate a commitment to robust cybersecurity practices that align with regulatory requirements.
Building a Zero Trust Model for Remote Applications
With the rise of remote work and the widespread use of cloud-based applications, the traditional security perimeter has all but disappeared. This shift necessitates a security model that assumes threats can come from anywhere, even from within the network itself. Zero Trust provides a structured approach to addressing these security challenges by emphasizing continuous verification, least privilege access, and a proactive defense strategy. Below is a detailed, step-by-step guide on how to implement Zero Trust for remote applications.
Step-by-Step Guide to Zero Trust for Remote Access
The first step in building a Zero Trust model is to clearly identify the organization’s perimeter and the assets within it that need protection. Unlike traditional perimeters that focus on network boundaries, a Zero Trust perimeter is defined by the resources that need securing, which may include:
- Applications: Web applications, SaaS platforms, and custom-built software that remote employees use for their work.
- Systems: Infrastructure elements such as servers, databases, and virtual machines.
- Data: Sensitive or mission-critical data stored within databases, cloud services, or on-premises data centers.
- Endpoints: Devices such as laptops, smartphones, and tablets that employees use to access corporate resources remotely.
By mapping out these assets, organizations can understand their threat landscape and prioritize security measures based on the criticality of each resource.
Implementing MFA is a foundational step in a Zero Trust framework, especially for securing remote applications. MFA strengthens access security by requiring users to provide at least two different types of authentication before they are granted access. These types typically include:
- Something they know: Passwords or security questions.
- Something they have: Physical or digital tokens, such as one-time passcodes (OTPs) sent via mobile apps or SMS.
- Something they are: Biometric verification, such as fingerprints or facial recognition.
MFA ensures that even if an attacker gains access to a user’s password, additional verification steps are needed to gain access to resources, significantly reducing the risk of unauthorized access. For remote applications, MFA can be integrated with Single Sign-On (SSO) solutions to streamline the user experience while maintaining high security standards.
Micro-segmentation is an advanced technique used to divide a network into smaller, more secure segments. This approach is vital for limiting lateral movement within a network if a breach occurs. In a Zero Trust framework, each segment is treated as an independent security zone, with access policies tailored to the specific needs of that segment.
Benefits of Micro-Segmentation:
- Granular Control: Organizations can set specific security policies for each segment, ensuring that only authorized users or applications have access.
- Containment of Breaches: Even if one segment is compromised, the attacker’s ability to move laterally is limited, reducing the impact of the breach.
- Improved Compliance: Micro-segmentation makes it easier to align with data protection regulations by isolating sensitive data in its own secure segment.
How to Implement Micro-Segmentation:
- Map Network Flows: Understand the communication patterns between applications, devices, and systems.
- Define Security Policies: Create access rules for each segment based on the identified communication flows.
- Use Security Tools: Deploy network security solutions that support micro-segmentation, such as next-generation firewalls or software-defined networking (SDN) tools.
- Monitor and Adjust: Continuously review and refine the segmentation strategy to adapt to changing needs and threats.
The principle of least privilege ensures that users are granted only the minimum access necessary to perform their job functions. This approach reduces the attack surface and limits the damage potential in case of compromised credentials or insider threats.
Key Considerations for Implementing Least Privilege Access:
- Role-Based Access Control (RBAC): Assign roles to users based on their job functions and define the access each role requires.
- Dynamic Access Policies: Use context-aware policies that adjust access based on factors such as user location, time of access, and device health.
- Access Reviews: Regularly audit and update user access levels to ensure that permissions remain aligned with current roles and responsibilities.
Steps to Enforce Least Privilege:
- Conduct Access Audits: Identify current access levels across the organization and remove excessive permissions.
- Implement Conditional Access Policies: Deploy access policies that respond dynamically to risk signals (e.g., requiring additional authentication if the user logs in from an unknown location).
- Automate Provisioning and De-provisioning: Use identity and access management (IAM) tools to automate user lifecycle management.
In a Zero Trust environment, continuous monitoring is essential to maintain security integrity. This involves tracking and auditing user behavior, access logs, and system activity in real-time to detect suspicious actions and respond promptly.
Components of Effective Continuous Monitoring:
- Log Collection and Analysis: Gather detailed logs of user activity and access attempts to create a comprehensive audit trail.
- Behavioral Analytics: Use machine learning and AI to identify abnormal behavior, such as an unusual pattern of data access or login attempts.
- Automated Alerts: Implement tools that can trigger alerts or initiate automated responses when suspicious activity is detected.
Steps for Continuous Monitoring and Auditing:
- Deploy Monitoring Tools: Use security information and event management (SIEM) systems to centralize log collection and threat analysis.
- Integrate Endpoint Detection and Response (EDR): Implement EDR solutions to monitor endpoint behavior and detect potential compromises.
- Regular Audits: Schedule regular reviews of logs and access records to identify patterns and update security policies as needed.
YouTube
OATH OTP MFA Explained: Easy Setup Guide for Stronger Security
Continuous Monitoring and Auditing
In a Zero Trust environment, continuous monitoring is essential to maintain security integrity. This involves tracking and auditing user behavior, access logs, and system activity in real-time to detect suspicious actions and respond promptly.
Components of Effective Continuous Monitoring:
- Log Collection and Analysis: Gather detailed logs of user activity and access attempts to create a comprehensive audit trail.
- Behavioral Analytics: Use machine learning and AI to identify abnormal behavior, such as an unusual pattern of data access or login attempts.
- Automated Alerts: Implement tools that can trigger alerts or initiate automated responses when suspicious activity is detected.
Steps for Continuous Monitoring and Auditing:
- Deploy Monitoring Tools: Use security information and event management (SIEM) systems to centralize log collection and threat analysis.
- Integrate Endpoint Detection and Response (EDR): Implement EDR solutions to monitor endpoint behavior and detect potential compromises.
- Regular Audits: Schedule regular reviews of logs and access records to identify patterns and update security policies as needed.
Key Components of Zero Trust for Remote Applications
The Zero Trust model is particularly effective in protecting remote applications, where traditional network boundaries are blurred. Implementing Zero Trust involves an integrated approach that covers various aspects of an organization’s IT infrastructure. Below, we explore the key components essential for deploying Zero Trust in the context of remote applications, each playing a critical role in fortifying security and preventing unauthorized access.
Best Practices for Zero Trust Remote Applications
Implementing a Zero Trust framework for remote applications requires careful planning and adherence to security best practices. Organizations must adopt a multi-layered approach to ensure robust security for remote access to corporate resources. Here, we outline the best practices for building and maintaining a strong Zero Trust model for remote applications, emphasizing least privilege access, adaptive MFA, user behavior monitoring, device compliance, and employee education.
Tools and Technologies for Zero Trust Remote Access
Implementing Zero Trust for remote access requires a suite of tools and technologies designed to secure various elements of an organization’s IT infrastructure. From network segmentation to endpoint protection and real-time monitoring, each tool plays a vital role in maintaining a robust security posture. Below, we explore essential tools and technologies that enable effective Zero Trust remote access, focusing on their capabilities and contributions to comprehensive security.

Conclusion
The successful implementation of Zero Trust for remote access relies on a combination of tools and technologies that secure identity, endpoints, networks, and user behavior. ZTNA solutions, IAM and SSO platforms, EDR systems, micro-segmentation tools, and continuous monitoring technologies work together to build a comprehensive Zero Trust framework. By leveraging these solutions, organizations can strengthen their security posture, minimize potential attack surfaces, and ensure that remote access remains secure against ever-evolving threats.
Best Practices for Zero Trust Compliance
Implementing Zero Trust principles can greatly aid in achieving and maintaining compliance with regulatory standards. Below are best practices to follow.
- Continuous Logging: Ensure that all access attempts and user activities are logged comprehensively. Logs should include details such as user ID, access times, device information, and the data or applications accessed.
- Audit Readiness: Regularly review and store logs in a secure, tamper-proof manner to ensure that they can be used for compliance audits and investigations.
- Automated Solutions: Use SIEM tools to aggregate and analyze logs for real-time threat detection and compliance reporting.
- Policy Framework: Create detailed documentation that outlines access controls, user roles, and permissions. This helps demonstrate adherence to compliance standards.
- Review and Update: Regularly review and update access policies to reflect changes in regulations, technology, and business processes.
- Employee Awareness: Ensure that employees are aware of access policies and understand their responsibilities regarding data security and compliance.
- Access Audits: Conduct periodic audits of user permissions to verify that access aligns with job roles and responsibilities. Remove or adjust permissions as necessary to uphold the principle of least privilege.
- Automated Tools: Use identity and access management (IAM) solutions to streamline the review process and ensure that permissions are updated as employees change roles or leave the organization.
- Data Protection: Apply encryption for data at rest and in transit to comply with requirements such as GDPR and HIPAA. This protects sensitive data even if an unauthorized entity gains access.
- Secure Connections: Enforce the use of secure protocols, such as TLS, for data transmissions to maintain compliance and protect against interception.
- Strong Authentication: Deploy MFA as a mandatory measure for accessing sensitive systems and data. This adds a critical layer of protection required by standards like PCI DSS.
- Adaptive MFA: Use adaptive MFA that adjusts the level of authentication based on risk factors, such as device type and location.
- Employee Training: Educate employees on compliance requirements and Zero Trust principles. Ensure they understand the importance of secure access practices, data protection, and incident reporting.
- Compliance Workshops: Conduct workshops and training sessions to keep staff updated on new regulations and the organization’s compliance practices.
About Me

Bert Blevins is a distinguished technology entrepreneur and educator who brings together extensive technical expertise with strategic business acumen and dedicated community leadership. He holds an MBA from the University of Nevada Las Vegas and a Bachelor’s degree in Advertising from Western Kentucky University, credentials that reflect his unique ability to bridge the gap between technical innovation and business strategy.
As a Certified Cyber Insurance Specialist, Mr. Blevins has established himself as an authority in information architecture, with particular emphasis on collaboration, security, and private blockchain technologies. His comprehensive understanding of cybersecurity frameworks and risk management strategies has made him a valuable advisor to organizations navigating the complex landscape of digital transformation. His academic contributions include serving as an Adjunct Professor at both Western Kentucky University and the University of Phoenix, where he demonstrates his commitment to educational excellence and knowledge sharing. Through his teaching, he has helped shape the next generation of technology professionals, emphasizing practical applications alongside theoretical foundations.
In his leadership capacity, Mr. Blevins served as President of the Houston SharePoint User Group, where he facilitated knowledge exchange among technology professionals and fostered a community of practice in enterprise collaboration solutions. He further extended his community impact through director positions with Rotary International Las Vegas and the American Heart Association’s Las Vegas Chapter, demonstrating his commitment to civic engagement and philanthropic leadership. His specialized knowledge in process optimization, data visualization, and information security has proven instrumental in helping organizations align their technological capabilities with business objectives, resulting in measurable improvements in operational efficiency and risk management.
Mr. Blevins is recognized for his innovative solutions to complex operational challenges, particularly in the realm of enterprise architecture and systems integration. His consulting practice focuses on workplace automation and digital transformation, guiding organizations in the implementation of cutting-edge technologies while maintaining robust security protocols. He has successfully led numerous large-scale digital transformation initiatives, helping organizations modernize their technology infrastructure while ensuring business continuity and regulatory compliance. His expertise extends to emerging technologies such as artificial intelligence and machine learning, where he helps organizations identify and implement practical applications that drive business value.
As a thought leader in the technology sector, Mr. Blevins regularly contributes to industry conferences and professional forums, sharing insights on topics ranging from cybersecurity best practices to the future of workplace automation. His approach combines strategic vision with practical implementation, helping organizations navigate the complexities of digital transformation while maintaining focus on their core business objectives. His work in information security has been particularly noteworthy, as he has helped numerous organizations develop and implement comprehensive security frameworks that address both technical and human factors.
Beyond his professional pursuits, Mr. Blevins is an accomplished endurance athlete who has participated in Ironman Triathlons and marathons, demonstrating the same dedication and disciplined approach that characterizes his professional work. He maintains an active interest in emerging technologies, including drone operations and virtual reality applications, reflecting his commitment to staying at the forefront of technological advancement. His personal interests in endurance sports and cutting-edge technology complement his professional expertise, illustrating his belief in continuous improvement and the pursuit of excellence in all endeavors.